Search: fišing
Vishing and Smishing
- Vishing is a cyber scam that takes place through calls
- Smishing is a cyber scam that starts via SMS or Chat messages
- The most common scams are aimed at collecting personal, business or financial data
Cyber frauds during holiday season
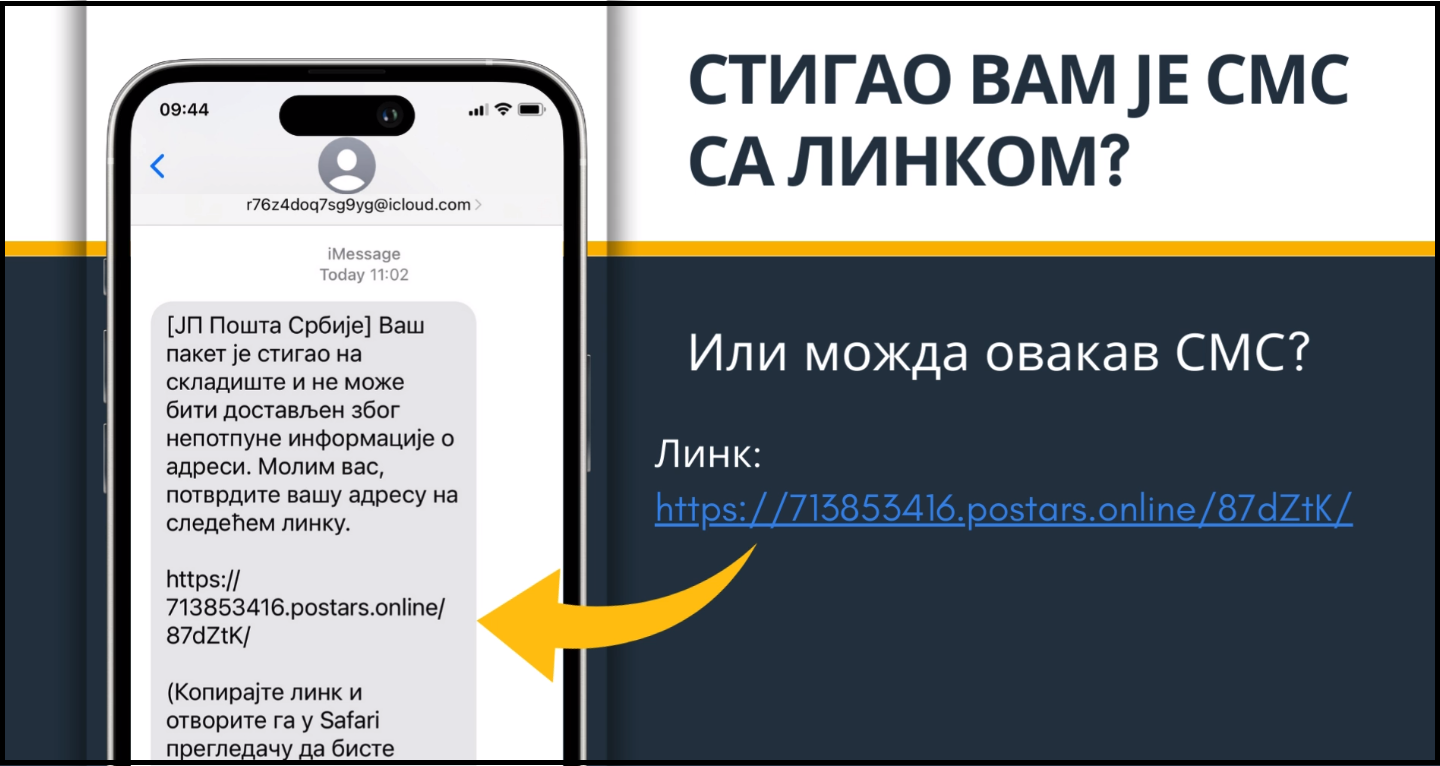
December being traditionally a month of holiday shopping and increased volumes of posted items, it is also a time of a growing number of cyber threat attempts. The National CERT of the Republic of Serbia therefore warns the citizens about current SMS phishing frauds targeting the users of postal services in this time of the year.
The attackers usually initiate the fraud by sending an SMS or text, containing an information about an unsuccessful postal item delivery attempt, along with a link to confirm address details. By clicking on the link, the victim is transferred to a fake web page of the PE Post of Serbia, where they are asked to enter personal information and credit card data. Disclosure of these personal data on the fake web page enables the attackers to clear the victim’s bank account.
The National CERT urges the citizens not to click on links contained in messages from unknown senders and to report similar incidents, in case they were defrauded.
More on this topic can be found in our video: ‘’SMS phishing frauds’’.
Phishing campaign - attempt to misuse the name of Telekom Srbija
The National CERT warns all citizens that a new phishing campaign is under way in which a malicious attacker is trying to misuse the name " Telekom Srbija". Users are being sent an email with the following content:
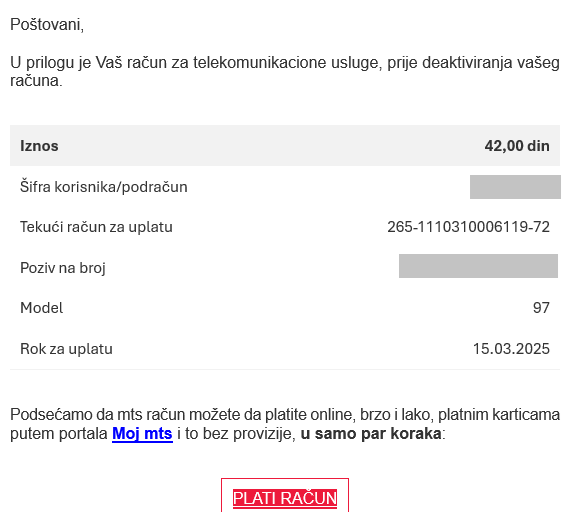
By clicking on the link, citizens are redirected to a fake website of Telekom Srbija, where the entry of personal data is required. By entering this information on the fake website, the ultimate goal of the attacker is achieved – withdrawal of money from the victim’s bank account.
The National CERT recommends that citizens avoid opening links in messages received from unknown senders, use official websites to follow notifications, and report an incident in case they have been scammed or if they notice a fraud attempt.
In addition, in order to improve the level of security for online shopping, the general recommendation for users is to make their payments via a special Internet card, intended exclusively for online payments. In this way, users can limit access to the funds available on the card, thus preventing attackers from clearing their dinar or foreign currency account.
Additional pecautionary measures for safe Internet and mobile device communication during state of emergency
The National CERT of the Republic of Serbia would like to inform and warn the citizens of a multitude of current online phishing and ransomware campaigns along with the existence of malicious applications for mobile devices. Beside the usual Internet based campaings targeting email addresses of the users, some SMS or mobile phone call based campaigns have also been observed.
These messages or malicious applications usually contains information on COVID-19, but a certain number of messages with different content have also been detected, since the users understandably switched to online and mobile communication during the state of emergency.
As part of preventive measures and actions, the National CERT urges all citizens to additionally verify the legitimacy of messages or calls requiring their personal data such as: user name and password, unique citizens identity number, current account number, credit card number including PIN and similar, so as to prevent the abuse of their accounts and personal data by the malicious Internet users.
Abuse of Institute of Public Health in phishing campaign
The National CERT of the Republic of Serbia informs the citizens and companies that a phishing campaign abusing the Covid-19 pandemic, targeting the public institutions and companies is under way. An email sent from address katarina.vojvodic@batut.org.rs, contains a fake notification from the Institute of Public Health of Serbia „Dr Milan Jovanović Batut“ about free distribution of protective gear to all registered individuals, and an attachment titled „preventive gear application form.pdf.zip“. This fake registration requires filling-in of the attached application form and it being sent by the end of working hours, thus abusing the emergency procedure and starting the download of malicous software - malware LokiBot. More on this malware can be found here
The National CERT advises all citizens and companies who receive such notification not to open the attachment contained in the email and report the phishing attempt to vtk@mup.gov.rs
Here you can find a warning issued by the Department of prevention of high tech crime, of the Ministry of Interior.
New abuse of Zoom platform against users of Microsoft Office 365
The National CERT wishes to warn the users of Microsoft Office 365 of a possible new phishing campaign where attackers try to get hold of the users’ Office 365 account login credentials.
The phishing message features fake notification about the Zoom communication platform account being taken down, with a link redirecting the user to a fake Microsoft login page. Based on the latest research, similar phishing messages appear to have reached over 50,000 email addresses so far. Taking over the credentials enables the attackers to access and abuse all the sensitive information stored in these accounts.
More info is available at the following links:
- https://www.bleepingcomputer.com/news/security/persuasive-office-365-phishing-uses-fake-zoom-suspension-alerts/
- https://abnormalsecurity.com/blog/abnormal-attack-stories-spoofed-zoom-attack/
So far, with the pandemic still increasingly present and a great deal of work being done from home, numerous abuses of communications platforms have been observed, among them the popular Zoom application. For more, please follow the National CERT’s link.
First regular meeting between National CERT and representatives of independent CERTs takes place
On April 28, 2021, the first regular meeting of the government body CERT, the National Bank of Serbia and independent ICT system operators' CERTs was hosted by the National CERT. The challenges discussed at the meeting pertain to ever growing sophisticated phishing campaigns, highlighting the necessity of systems for detection and prevention of such types of attacks, as well as raising awareness both with the employees and the general public about this threat. Particular importance was placed on a continuous exchange of information on current events and activity plans for the future.
In accordance with the Law on Information Security, the National CERT, government body CERT and independent ICT system operators' CERTs maintain constant cooperation in the aim of improving the cyber security of the Republic of Serbia.
New phishing campaign that misuses the name of the National Bank of Serbia
The National CERT of the Republic of Serbia informs the public about an ongoing phishing campaign that misuses the name of the National Bank of Serbia.
Scams are being delivered to citizens via email or social media, requesting the entry of personal and financial information, which attackers can use to withdraw funds from citizens' accounts.
The announcement from the National Bank of Serbia is available at the following link.
Meeting between National CERT and Special CERTs
In order to improve cooperation and strengthen public and private partnerships, the National CERT held its first regular meeting with Special CERTs. The representatives of Special CERTs presented their activities over the previous period, as well as challenges they encountered in their everyday work. Particular importance was placed on the importance of a continuous exchange of information about current activities regarding the National CERT and Special CERTs. The discussion was also held about current phishing campaigns, with a conclusion to improve the education of both employees and general public.
The National CERT, operating under RATEL, keeps a registry of Special CERT's in the Republic of Serbia, in accordance with the Law on Information Security. The Special CERTs perform tasks of prevention and protection against security risks in the area of cyber security. For more details on services provided to users, please visit: https://www.cert.rs/en/evidencija-certova.html